Estimated Read Time: 6 Minutes
Public Internet Connection Risks
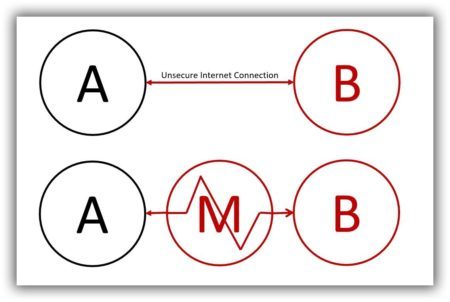
I think most people know or suspect that it’s unwise to purchase items over a public Internet connection but they might not know why. One of the reasons is because of a possible man-in-the-middle (MITM) attack. A MITM attack is when someone inserts him or herself into the middle of your, and the website you are visiting’s, Internet connection and impersonates both parties to gain access to sensitive information like userids, passwords, name, address, telephone number, and credit card data. As you can imagine, this creates opportunities for identify theft.
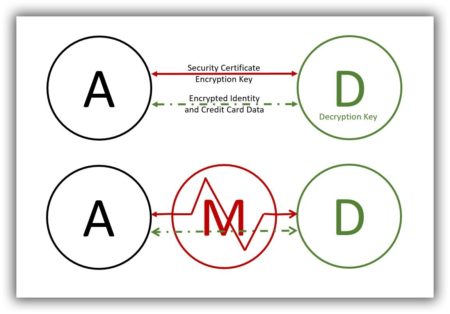
Let’s say, for example, Ann (A) is in her favorite coffee shop browsing Best Buy (B’s) eCommerce website and wants to make a purchase. There is nothing to stop a malicious man-in-the-middle (M) from inserting himself into Ann and Best Buy’s conversation. He can capture, and possibly alter, the data that gets transmitted. If Ann makes a purchase, he can adjust the order quantity and/or steal her identity. Ann and the website she’s visiting are both at risk.
HTTPS Protects In-Transit Data
Enter HTTPS.
HTTP (without the “s”) stands for HyperText Transfer Protocol. It is the standard and agreed-upon format for transmitting data between two devices on the Internet. Just like the default language of aviation is English, the default language of computers is HTTP.
HTTPS, on the other hand, stands for HyperText Transfer Protocol Secure. It is a way to help protect data that is moved back and forth between your browser and the computer you are communicating with. How? It layers a security certificate and encryption on top. Here’s how it works.
Let’s revisit Ann’s shopping experience and pretend she is shopping at Adorama (D) instead of Best Buy. Adorama has a secure (HTTPS) website. When Ann uses her browser to connect with Adorama:
- Her browser requests and Adorama sends, an independently verified security transaction that certifies the web server Ann is trying to connect to does, in fact, belong to Adorama.
- Adorama also sends an encryption key to Ann’s browser. The key will be used to encrypt or scramble any subsequent transactions between the two.
Only Adorama has the decryption key. Even if a malicious man-in-the-middle intercepts their exchange, he or she will not be able to alter, delete, or make any sense of subsequent conversations. Both parties are protected.
HTTPS is added security but not total protection. Already some folks are figuring out ways around the certification process. It’s not perfect, but it is a step in the right direction and likely to improve even more as time goes on.
Why Convert Now?
HTTPS has been around since 1994. Why is there a sudden push for everyone to convert? What changed?
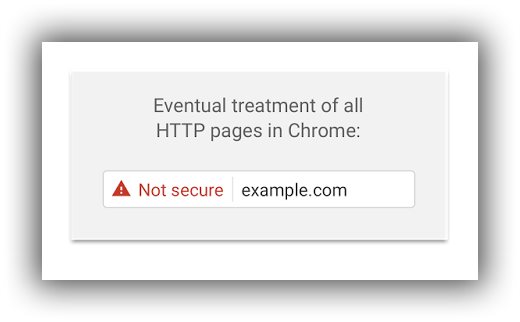
Concerned that users are not recognizing or heeding Google’s previously neutral and ambiguous labeling of unsecure websites, on September 8, 2016 Google announced that beginning in January 2017, it will explicitly start labeling all HTTP connections as not secure.
“Historically, Chrome has not explicitly labeled HTTP connections as non-secure. Beginning in January 2017 (Chrome 56), we’ll mark HTTP pages that collect passwords or credit cards as non-secure, as part of a long-term plan to mark all HTTP sites as non-secure.
In following releases, we will continue to extend HTTP warnings, for example, by labeling HTTP pages as “not secure” in Incognito mode, where users may have higher expectations of privacy. Eventually, we plan to label all HTTP pages as non-secure, and change the HTTP security indicator to the red triangle that we use for broken HTTPS.”
This is the visual they shared that illustrates what they mean by a not-secure label.
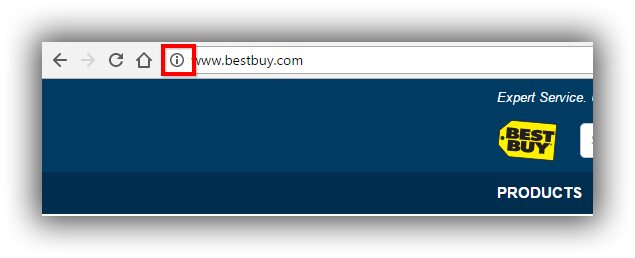
So far, we have not seen the “not secure” label. We have only seen the already familiar gray circled letter “i” displayed in browser address bars when websites are not secure. Here’s an example using Best Buy’s website (below).
Google has, however, amped up their labeling of secure websites, like Adorama’s (below). Labeling now includes a green padlock, the word “Secure”, and the green letters “https” on all websites that have been completely and successfully converted.

Implications For Website Owners
If you own a website that captures userids and passwords or credit card data, you will soon be labeled as “Not Secure” when visitors are using the Chrome browser. This is bound to raise concerns and deter people from wanting to transact with you, especially if you’re asking for any type of personal data – email addresses, for example, to build your mailing list. Website visitors will easily be able to recognize unsecure websites and find better, more secure, alternatives.
If you own an informational (non-eCommerce) website and think you’re off the hook, think again.
Non-eCommerce website owners also risk losing the trust and confidence of website visitors. 25% of the world’s websites are built with WordPress, a content management system that is accessed, administered, and maintained using a Userid and password. Joomla and Drupal, WordPress’s closest competitors, also use userids and passwords. These sites will eventually be flagged as non-secure unless they are converted over to HTTPS.
As a website owner, you should also be aware that anyone who intercepts the transmission of userid and password data will be able to add, change and delete content on your website. It’s not only website visitors who are at risk. Website owners also need to protect their data.
Implications For SEO
In addition to the obvious benefit of securing the trust and confidence of your audience in addition to the securing your and your customer’s login, identification, and credit card data, there is also a search engine optimization (SEO) benefit when you migrate over to HTTPS.
Google announced HTTPS as a ranking factor in 2014.
“For now it’s only a very lightweight signal — affecting fewer than 1% of global queries, and carrying less weight than other signals such as high-quality content — while we give webmasters time to switch to HTTPS. But over time, we may decide to strengthen it, because we’d like to encourage all website owners to switch from HTTP to HTTPS to keep everyone safe on the web.”

At the time, the lightweight incentive wasn’t enough to incent most non-eCommerce website owners to migrate because of the work involved and the potential to lose SEO equity.
When you convert your website to HTTPS, you are effectively changing your Internet address. That means you should give Google (and other search engines) a “change of address” notification, also known as a 301 or 302 redirect. Traditionally, a redirect diluted your SEO equity or ability to rank by as much as 15%. That recently changed.
In February 2016, Google’s John Mueller announced that SEO equity or PageRank will no longer be lost when a 301 or 302 redirect is used in conjunction with an HTTP to HTTPS migration. Skeptical SEO’s doubted the truth of this but in July 2016, another Google employee, Gary Illyes, tweeted the same thing and Barry Schwartz at Search Engine Land confirmed it. There is no longer an SEO penalty when you implement HTTPS. The previously lightweight signal could actually help boost your rankings.
Now Ann and other website visitors can feel safe knowing secure-labeled websites will protect their identity and data. Website owners can too.
If you decide to move forward, here is an easy-to-use Excel HTTP to HTTPS Conversion Checklist you can use to help streamline the transition.



Leave A Comment